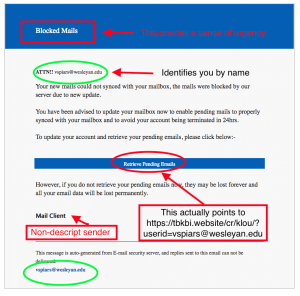
Anatomy of a PHISH and the use of Social Engineering
PHISH is defined as a method of getting you to provide credentials or otherwise profit the originator of the email independent of who is harmed. Social Engineering is roughly defined as manipulating you to do some one else’s bidding but having you think it is for your benefit. Once the dust settles you find yourself the victim and either poorer, having compromised credentials in the wild or both.
Let’s examine an example PHISHing email I received. With this I hope to show you how to identify and avoid falling for their trickery.
Subject—the subject of the email was designed to get your attention—“Blocked Mails”. No one wants to be missing email. This entices you to rad the actual email.
In the opening line it identifies me by name. It gives some level of legitimacy from the start. “Only someone like Wesleyan or Amazon know who I am.” This is not true. They may have done a little research as to who is employed at Wesleyan and sent this to you (all personnel at Wesleyan).
Bad grammar—Who says “Mails” when referring to email? The first sentence has more grammar issues. Now, yes, you can have a legitimate email from a person like me that just can’t spell for beans and occasionally, misses things Spell Check flags. Or doesn’t have Spell Check enabled. But aside from the incorrect or mangled words the grammar flows, correctly. In this example the grammar is incorrect—“Your new mails could not synced with your mailbox, they mails were blocked by your server due to new update”. There are additional examples but you get the idea.
Vocabulary in text selected to give it gravity and trigger your sense of urgency. This will then cause you to make less-informed decisions clouded by confusion. You don’t want to do anything wrong at work. Your reputation is all you have to show you are a solid and reliable employee. “If I’m missing email it could be something important. I don’t want to miss anything important!” This will help you bypass and ignore all of your tingly senses and little voices saying “This doesn’t look quite right”.
The Link—If you hover over a link on a web page or active email hyperlink it will show you (either at the bottom of your browser or next to the cursor) the actual path of the link. I can make a link display as anything. I can say it is “Your new sweepstakes prize” and point it to iPhones.com. It is the underlying path of “https://www.iphones.com” you are interested in. The example below shows the actual link has nothing to do with Wesleyan or Wesleyan.edu. It takes you to “This actually points to
https://tbkbi.website/cr/klou/ and appends your email address (?userid=vspiars@wesleyan.edu). This is to auto-fill the user ID field to “assist” you and get you to think this is still legitimate. “How else would the bad guys know my email address?”
The Signature—“Mail Client”. Who signs it “Mail Client”? Even the automated system it purports to be would have something a little more identifiable. If the signature is generic then question it. It is by no means a guarantee it is a fraudulent email but it is another piece of information that, cumulatively, can indicate fake/PHISH/SPAM email.
They only need to be lucky, once. We need to be careful and error-free, every day.